Hey guys, I’m pretty sure you must have come across or heard of the information security field Social Engineering (SE) . In this article, I’m going to introduce you to what social engineering is, the types of social engineering attacks, the various types of social engineers, and how you can protect yourself from being a victim of it.
Let’s get started!

What is Social Engineering?
Social Engineering is a deceptive method used to exploit people to gain access to unauthorized information for use. Social Engineering acts involve gaining unauthorized access to things on the web, obtaining information, and manipulating the target psychologically to take certain actions. Attacks caused by social engineering can take place online, through physical conversation and various interactions.
Social Engineering Attacks?
- Phishing
- Tailgating
- Pretexting
- Baiting
- Ransomware

Phishing:
This type of social engineering attack is often used to steal users’ login credentials, credit card details, and user data. Attackers can disguise themselves as a trusted corporation, send fake emails, fake text messages, or clone a site just to get user information so they can exploit them for illegal purposes.

Tailgating:
Also known as piggybacking, it is a social engineering attack where the attacker gets inside a restricted place without authorized access. This type of attack takes place when the tailgater(attacker)follows authorized personnel to gain access into the restricted area.

Pretexting:
It is a form of social engineering attack where the attacker creates a false identity with the sole purpose of tricking the targets to give out delicate information that can be used to gain access to their system.

Baiting:
It is a social engineering attack where the attacker makes false promises to the target by luring them into a trap. Baiting attacks can happen when the attacker promises to reward the target when the target takes some steps. This attack occurs mostly as a result of the target's “greed”.
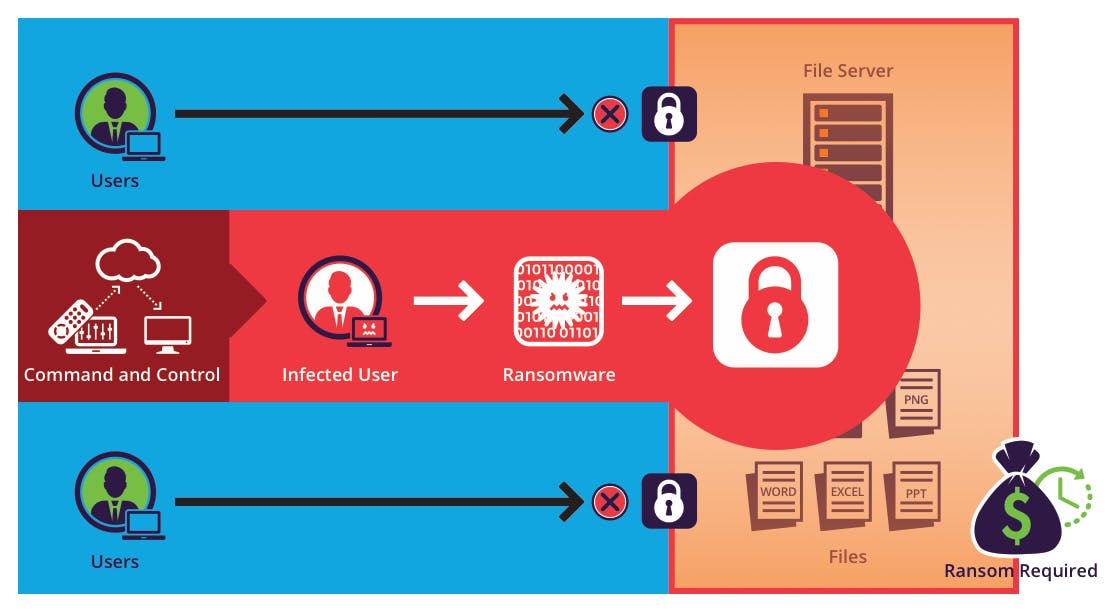
Ransomware:
It is a malicious software that locks up your computer resources or files to restrict your access to them (basically, it encrypts the files ) and you are asked to pay some ransom to get your files (to decrypt them).
Types of Social Engineers?
Social engineers include the following but are not limited to:
- Hackers
- Spies
- Penetration testers
- Identity thieves
- Scam artist
How to avoid social engineering attacks
- Ensure multi-factor authentication(MFA) is set up on all your social media accounts.
- Change your spam email settings & set your spam filter to “High”.
- Install antivirus software on your computers and ensure that all your antivirus software is up to date.
- Implement DMARC(Domain-based Message Reporting and Conformance). DMARC is a technical standard that protects email senders and recipients from spam, spoofing, and phishing.
- Don’t give out your password to anyone online.
- Ensure you look out for the kind of URLs(Uniform Resource Locator)you click. URLs with “https” are secure sites and information exchanged on these sites are encrypted. Sites with the URLs having “http” are prone to attacks and information shared on sites can be exploited by hackers. You should always watch out for the kind of URLs you click.
Conclusion:
In this article, we walked through what social engineering is and forms of social engineering attack. Then, we also outlined the various types of social engineers we have and how we can avoid social engineering attacks. So there you have it! I hope you all enjoyed the article. I hope to write some more interesting and educating topics like this. If you have any questions as regards this article please do not hesitate to reach out to me on Twitter: @Stefán

